Learn the 8 fundamentals we recommend to establish an effective Enterprise Risk Management process from the ground up, which will set the stage for a successful GRC program rollout.
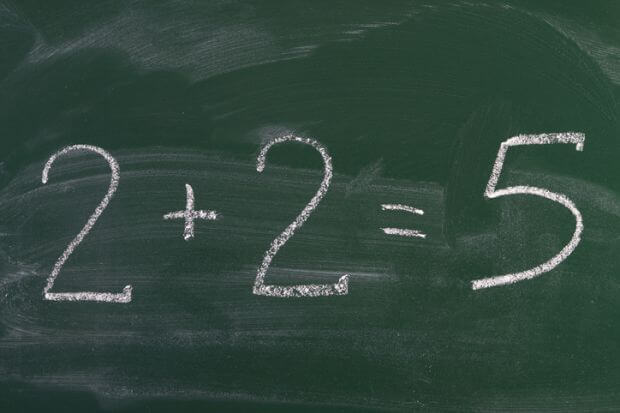
Normalizing Risk Scoring Across Different Methodologies
If the "textbook" definition of risk scoring is Risk = Likelihood x Impact, then a Severe (5) impact and an Almost Certain (5) likelihood should have a score of 25, right? The answer isn't quite so simple...
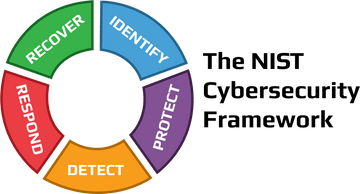
Simplifying the NIST Cybersecurity Framework with SimpleRisk
Learn how to use SimpleRisk's Import-Export and Risk Assessment Extras in order to efficiently use the NIST Cybersecurity Framework's controls to assess your organization's risks and perform a control gap analysis.

Quickly Customize Your Risk Management Program (using SimpleRisk.com)
When I first released SimpleRisk as a free and open source risk management tool at the BSides Austin conference...

Why Management Doesn't Understand Your Security Woes
Has the number of security issues you deal with on a routine basis ever made you feel a bit like Atlas carrying the ...


