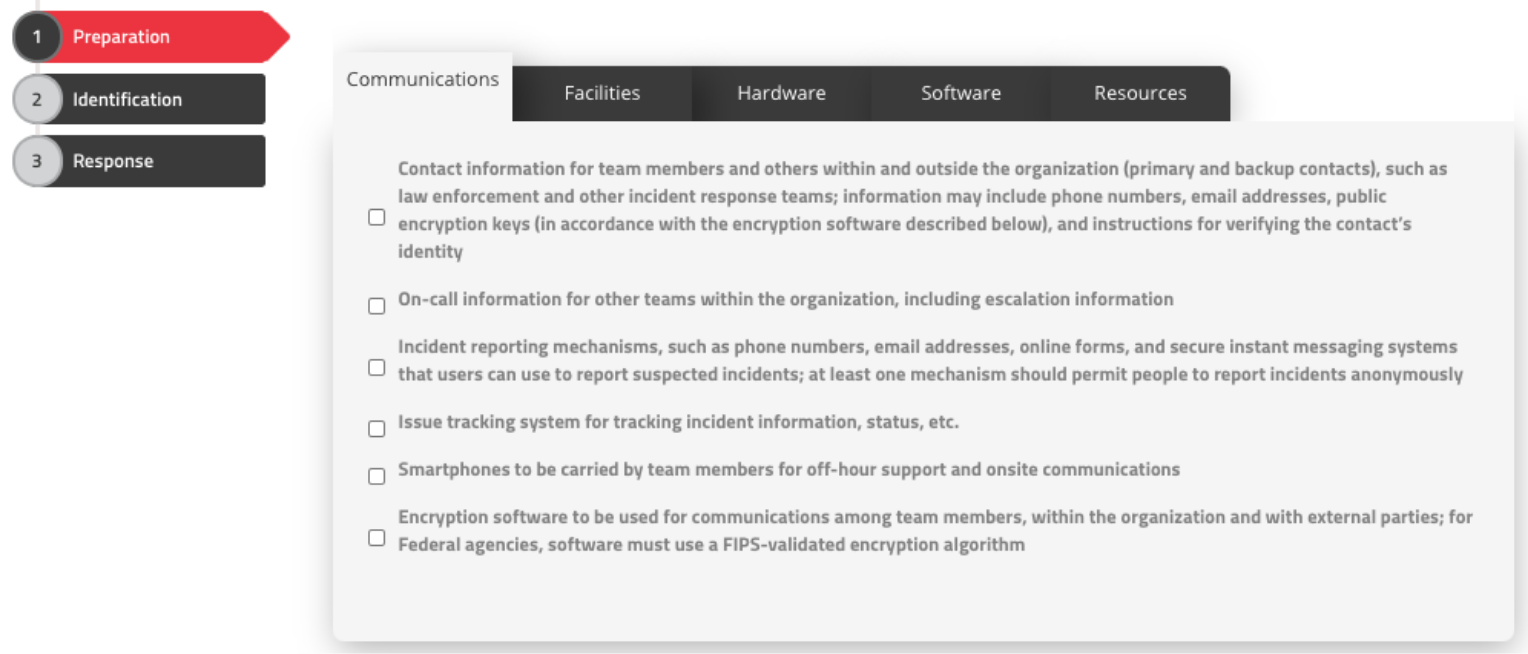
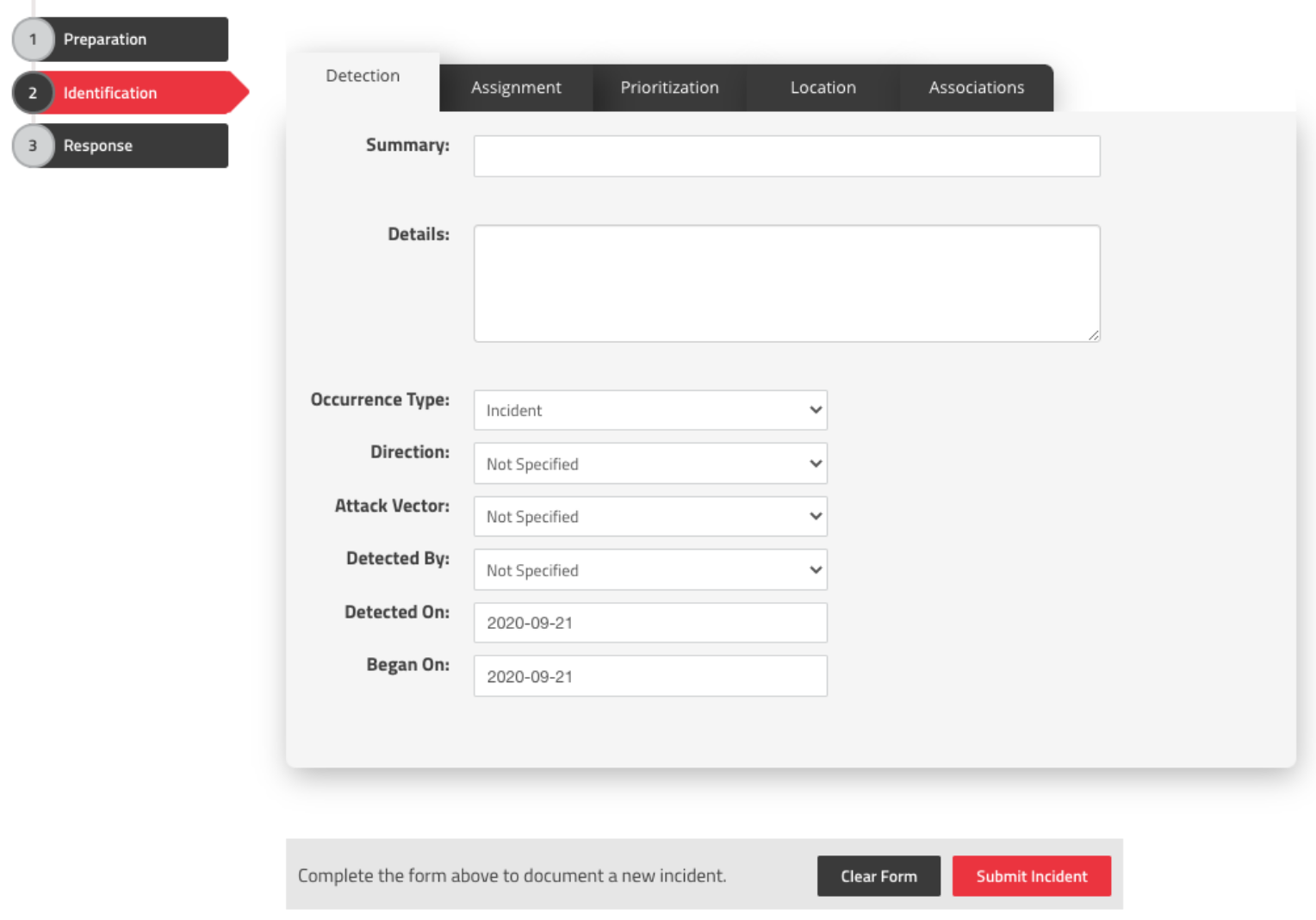
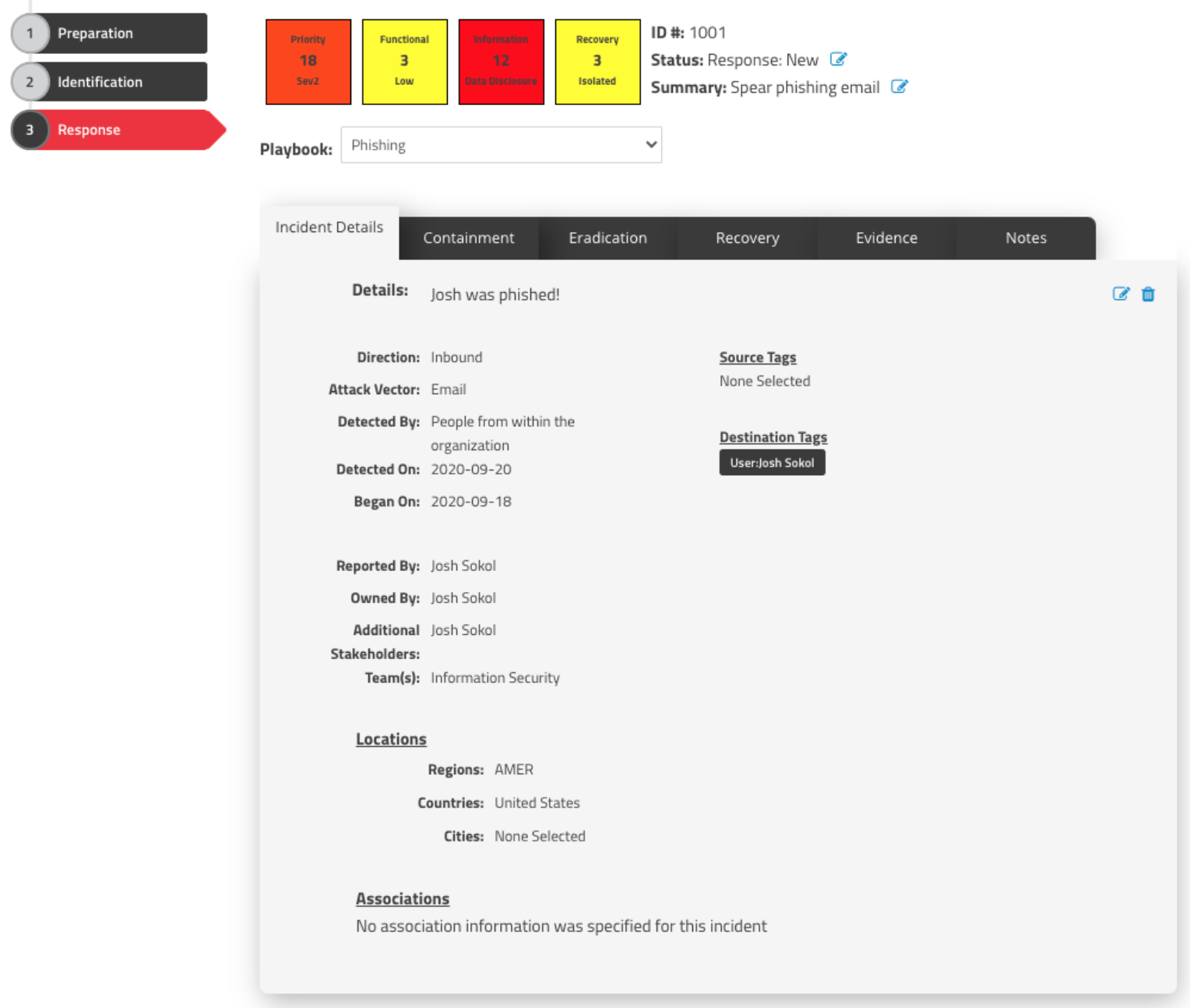
About SimpleRisk
SimpleRisk is a comprehensive GRC platform that can be used for all of your Governance, Risk Management and Compliance needs. It boasts functionality that is comprehensive enough to be utilized by some of the largest organizations on the planet while presenting a user interface that is so simple and intuitive it can be used by the least technical people in your organization.
Our SimpleRisk Core can be downloaded for free from our website, installed in minutes, and provides all of the capabilities that you need when first launching your GRC program. As your organization grows and matures its processes, our SimpleRisk Extras are licensed modules that provide enhanced functionality on par with competitors that cost orders of magnitude more and require months of professional services to install and configure. There's no need to waste all of that time and money when you can be up and running with SimpleRisk today.