On March 29, 2019, Alex Polimeni and I presented at the BSides Austin conference on some of the work we've done for National Instruments with respect to using the NIST Cybersecurity Framework (CSF) as the foundation for an assessment of the organization's cybersecurity maturity. For those who aren't familiar with the NIST CSF, it splits cybersecurity best practice activities up into five functions: Identify, Protect, Detect, Respond, and Recover. Then, each of those functions are split into several categories. For example, the Identify function is split into the categories of Asset Management, Business Environment, Governance, Risk Assessment, Risk Management, and Supply Chain Risk Management. There are a total of 23 of these categories in the NIST CSF framework. Lastly, each of those categories is then split into several sub-categories with a total of 108 of these sub-categories that can be used as controls for your organization.
Alex and I figured out that we could gauge our current maturity for each of these sub-categories by assigning each one of the following values:
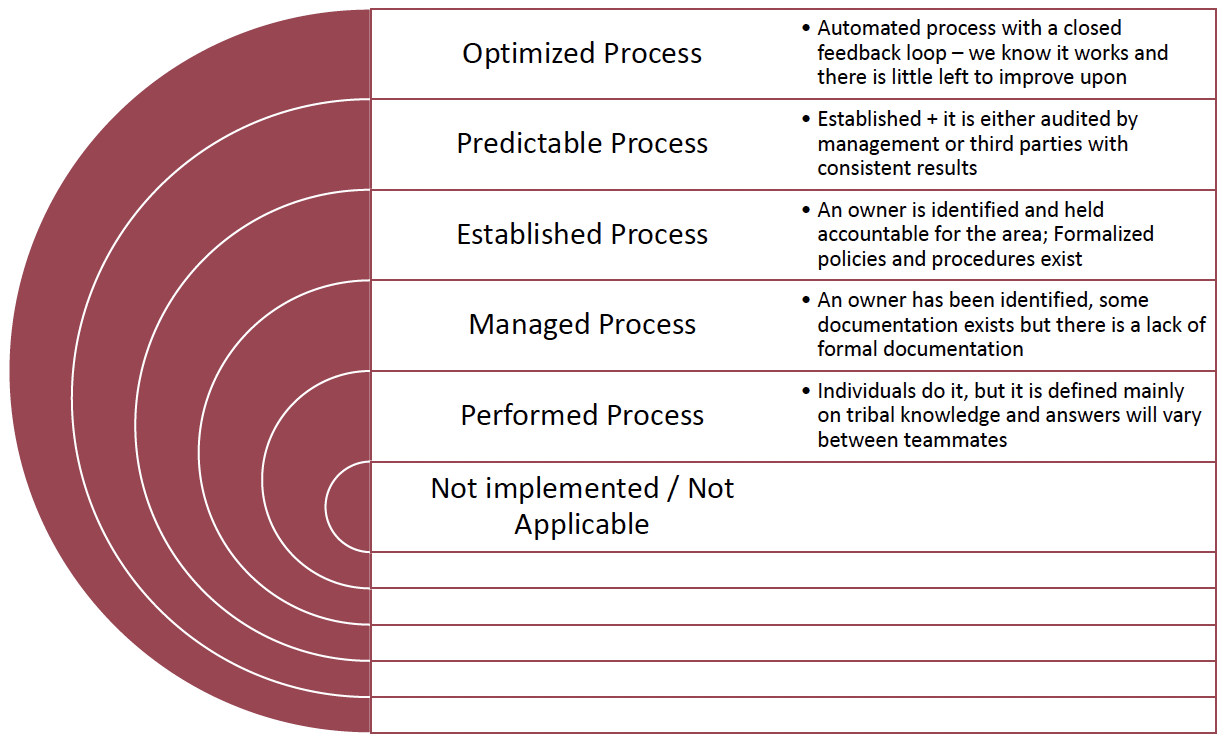
Once we finished assessing our current maturity, we could use these same maturity values to determine our desired state of maturity. The resulting spreadsheet might look something like this:
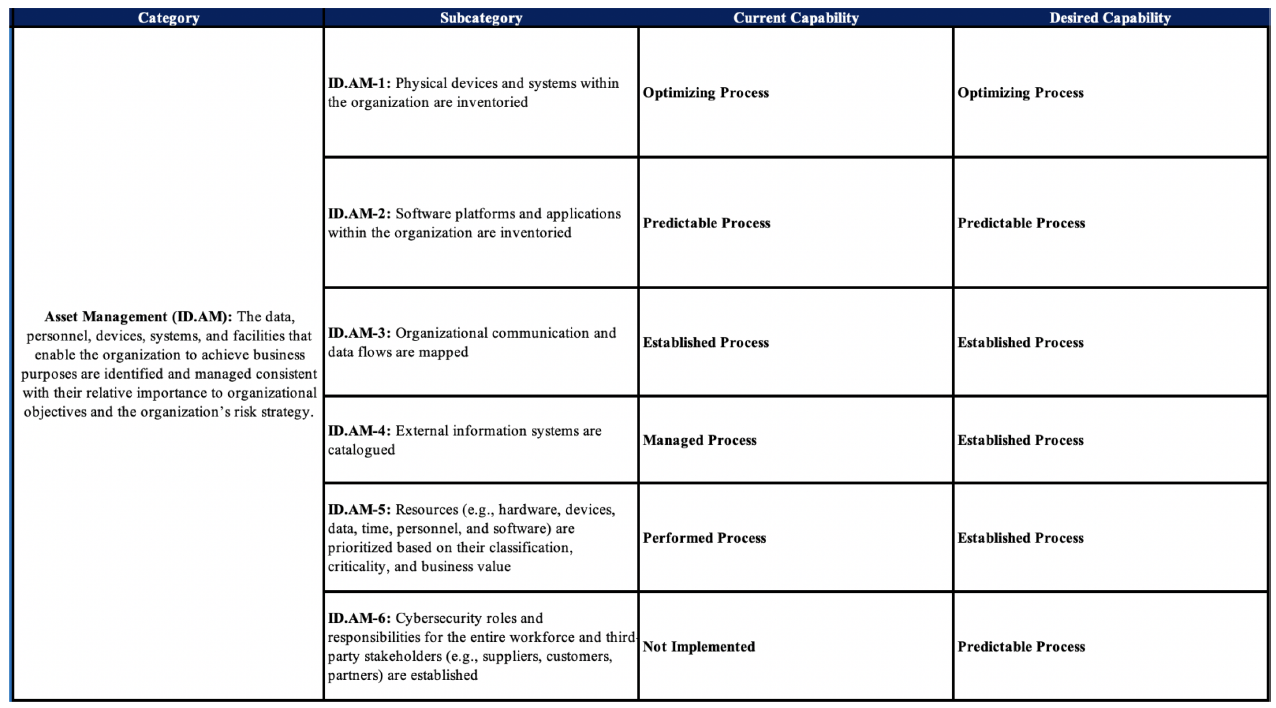
We would then expand on each of these by defining why we made these decisions and assigning owners for each. Next, we could compare our current capability to the desired capability and anyplace there is a gap, we documented a risk for it in SimpleRisk.
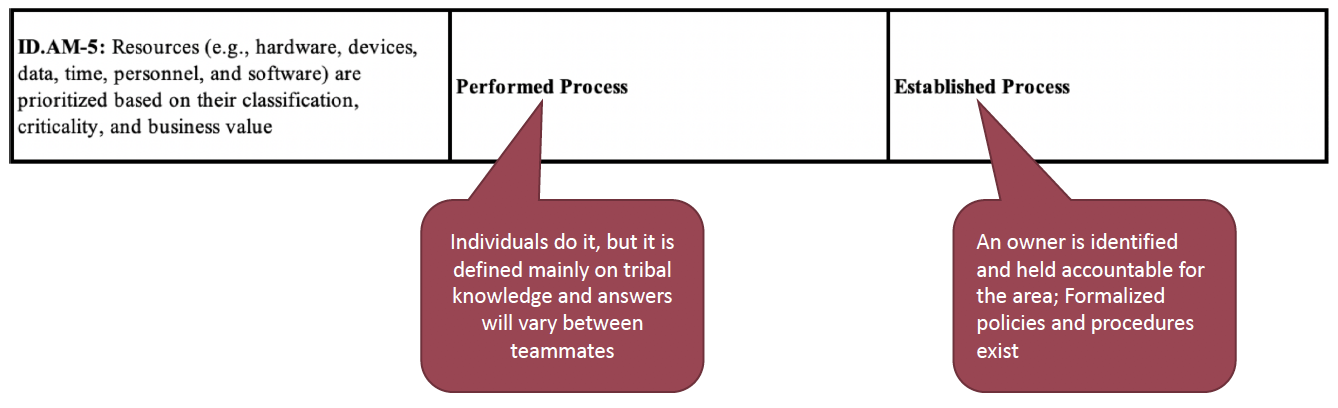
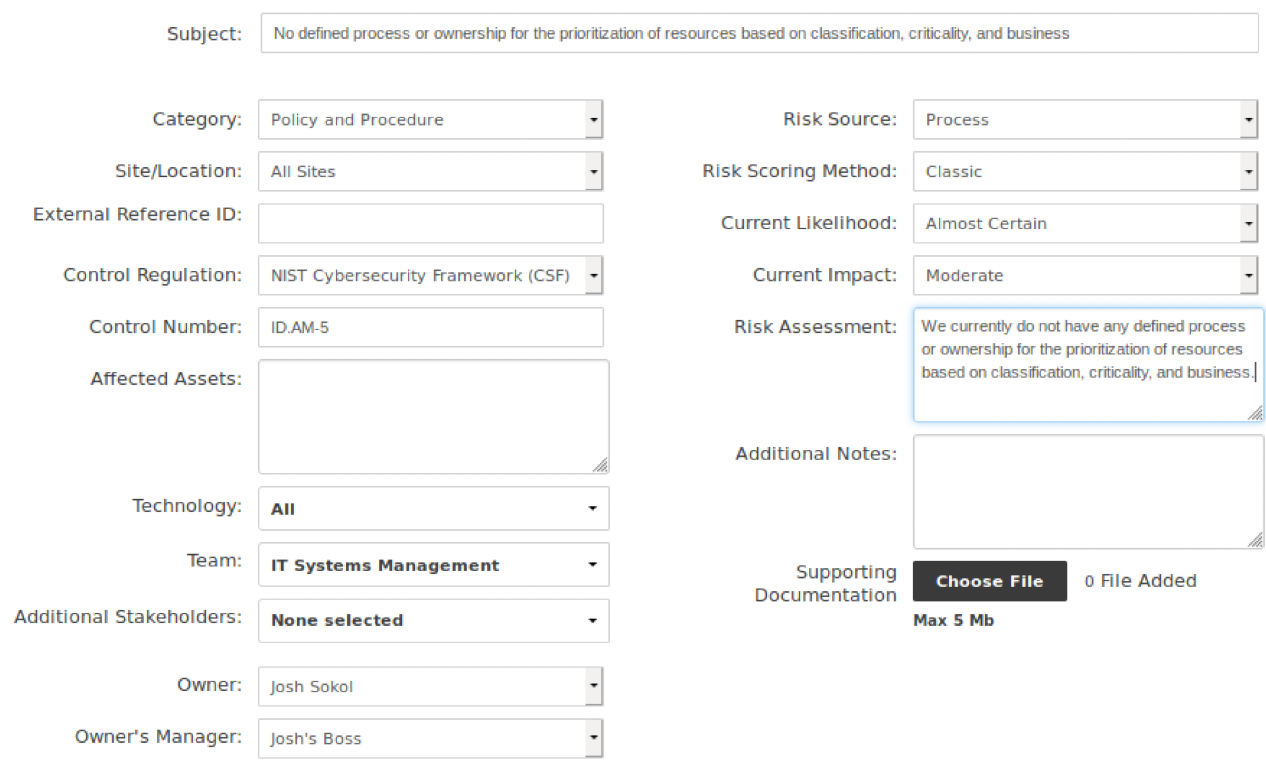
Because we were using SimpleRisk to document the risks, our risk scores were automatically calculated. The next step was to plan our mitigations for these risks and then prioritize what to work on first. This would become the basis for our roadmap.
We determined that work would be prioritized based on four factors. The first was "Burning Fires". These were the high priority items that could cause serious business interruption or financial loss. The "High Risk Report" in SimpleRisk would be key to identify these risks. The next was the "Quick Wins". These were the low-hanging fruit that could be accomplished without much outside assistance or minimal resource investment. By defining a mitigation cost value when planning the mitigation for these risks, these quick wins were easily highlighted by SimpleRisk's "Risk Advice" report. Third was the "Long-Term Work". These were thematic issues where a project was likely necessary to address multiple risks. SimpleRisk gave us the ability to define these projects in order to group the risks together and report on them. Lastly was work based on management goals and objectives. These were areas where the company had ongoing goals and initiatives that could be supported by these projects.
I won't lie...this was a fairly significant amount of effort, but the result was invaluable. All said and done, we now have spider charts outlining the differences in our maturity across the various functions and categories, we have a prioritized list of risks in our environment, and we have a roadmap based on those risks to articulate the future of our security program. This level of understanding is relatively unheard of in most security programs.
They did not record the presentation, unfortunately, but if you'd like to see it for yourself, feel free to download it here. For the official record, all of the capabilities we leveraged with SimpleRisk, as described above, are part of the free and open source SimpleRisk Core. Consider a free download of SimpleRisk today.
Related Articles:
Why Management Doesn’t Understand Your Security Woes
Simplifying the NIST Cybersecurity Framework with SimpleRisk